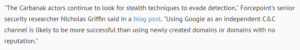
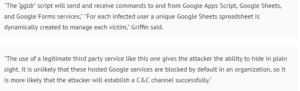
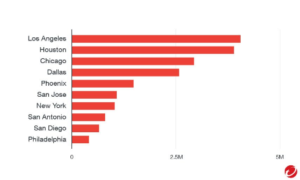
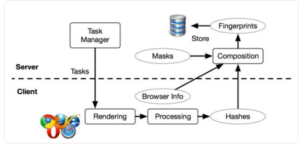
“The world of reality has its limits; the world of imagination is boundless”
~Jean-Jacques Rosseau [1]
That statement is wrong, and the proof is right in front of you. The act of using a computer or smartphone to read this blog post demonstrates the extent of which technology has permeated everyday life. The world is evolving, changing, and growing; every new invention and innovation further blurs the fine line between science fiction and science fact. Previously inaccessible, the realm of imagination is now more tangible than ever with reality shedding its limits and metamorphosing into a world of endless possibilities. However, out of all the technological wonders conceived by the Digital Age, one soars above the rest when it pertains to the paradoxical fusing of imagination and reality.
Virtual reality (VR) is quite the oxymoron. When it pertains to lenses and mirrors, “virtual” describes rays of light that appear to cross paths but do not physically intersect. VR is much the same; it is a reality that appears to exist, but it does not actually exist. It is a peculiar concept, one that doesn’t seem like it would ever leave the drawing board.
Why bother pouring real time and effort into technology that only creates something fake?
Yet despite the backwards logic of the idea, VR technology has skyrocketed in the past decade. Many of the major tech companies have funneled millions of dollars into VR development:
- Samsung’s Gear VR headset
- Google’s Daydream, Cardboard, Tilt Brush, and Earth VR
- Microsoft’s Windows Mixed Reality
- HP’s Z VR Backpack PC
- Amazon’s Sumerian platform
However, even though the term “Virtual Reality” is little over 30 years old, its history stretches back hundreds of years to the times of old panoramic paintings; artwork so large and wide, it seemed to transport the viewer into whatever scene it was depicting. You can find more information on VR’s intriguing history here.

Despite VR’s prominence in the minds of wealthy investors and visionaries in the past centuries, the general public were forced into spectator positions: VR technology was simply too expensive, not immersive enough, and therefore not popular. [2] That all changed with the introduction of a new industry: Video games.
From its modest birthplace at Brookhaven National Laboratory, the growth of video games in the past few decades has been nothing less than exponential. [3] You would be hard-pressed to find a person who has not heard of Mario, Zelda, or Pikachu. In these video games, players were given fantasy worlds, immersive stories, and new adventures, however, we were only peering through the window, waiting on the welcome mat in front of the door between us and the virtual world of video games.
Then came the key.
In March of 2013, Palmer Luckey released the DK1 (Development Kit 1), the first purchasable VR headset from his company: OculusVR. This was big. Never before had a virtual reality headset so evenly balanced quality and cost, allowing the general public to have access to VR, making virtual reality a reality. Even though this prototype was not without faults, its impact was felt around the globe, sparking a revolution in the gaming industry and reviving VR’s popularity.
Nowadays, there are various other VR headsets and related companies (VIVE and PlayStation to name a few). The amount of VR-interactive games has increased a hundredfold, encompassing everything from Minecraft to Resident Evil to even a Rick and Morty simulator (I’m not kidding). Even Pokémon GO incorporated augmented reality (AR) concepts, although its initial popularity was rather short-lived.
Despite its growing prominence in the gaming industry, VR’s presence in society and culture is not restricted to pixelated recreations of Pickle Rick. New York bestseller Ready Player One revolves around a global MMORPG-esque VR game where players can explore a universe of virtual worlds. Ender Wiggin utilizes VR simulations when fighting the Buggers in Ender’s Game. And who could forget about The Matrix trilogy which introduces a dystopian society where sentient machines have trapped humans in a simulated reality.

But as far as we know, we only have one reality. In that sense, VR seems like a fruitless endeavor to achieve the impossible. However, isn’t achieving the impossible what humanity does best? Sending a man to the moon, curing Polio, building the Great Pyramids, our lives are spent chasing dreams, striving to turn the impossible to possible, imagination to fact, virtual reality to reality. Only time will tell what the future holds in store because we have only just begun to tap into the potential of VR, something truly boundless.




 4
4